It's 2025. We, as humans, have created the opportunity to come much closer than we have ever been. We ease this interconnection for ourselves with the large network that we call The Internet. But with this global interconnection, we are more prone to losing our online privacy and anonymity than ever before.
Internet Growth and Online Privacy Concerns
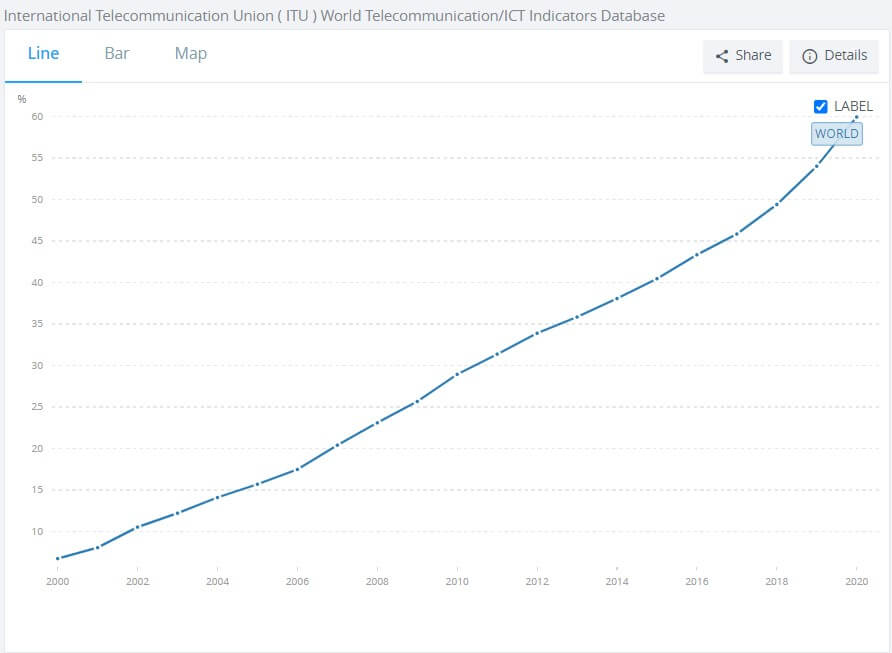
Source: The the International Telecommunication Union, World Telecommunication/ICT Development Report, and database, and World Bank estimates
According to the World Bank, we started this century with 6.7 % of the world on the Internet. Today, that figure has risen to 60 %. It is a remarkable increase.
Any system that grows at this rate is quite likely to amplify the scale of its problems. Likewise, this global Internet village has its set of global challenges. One such problem is the role of online privacy and anonymity in this new online society. As is the norm today, we expect the solution to work at the push of a button. In his 1986 satirical piece Homage To Qwert Yuiop: Essays, Anthony Burgess famously said,
To be left alone is the most precious thing one can ask of the modern world.
This quote had a very different meaning back in 1986 English society. But, the thought has equal value today when we talk about online privacy. Privacy is essential for everyone. It is important to be in absolute control of your identity, safeguard your sensitive information, and be able to make an unbiased choice. It is possible only when the choices presented to you are not limited by the online information collected about you.
Why Online Privacy Matters

When it comes to our offline world, we strive to maintain some degree of privacy and anonymity. Will we be comfortable with the post office reading all our emails? We buy curtains, lock our doors, and put passcodes on our mobile phones. Do we know anyone who will willingly give us their signatures on a blank paper either, just because they have nothing to hide?
When it comes to the online world, we are comfortable with most of these behaviors. We give out personal information such as name and email address to sign up for websites. We readily give our credit card information, social security number, date of birth, and digital signatures. This data goes hopping through servers that other people own, people we know nothing about.
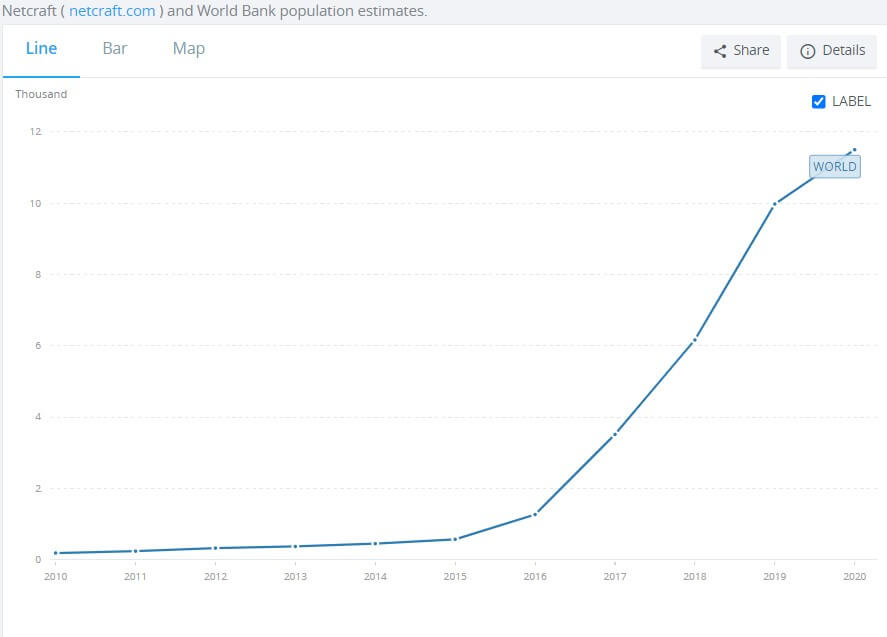
Source: Netcraft and World Bank population estimates
Online Privacy concerns have gradually risen over the last few years. After the NSA document leaks by Edward Snowden in 2013, people are much more aware of WhatsApp Privacy and Facebook Messenger privacy. Even WhatsApp recognized this necessity and made its services much more secure by adding encryption. Apple too had to add better encryption services to their iPhone 7 offering way back.
Apple's new App Tracking Transparency introduced in iOS 14.5 gives iPhone users more control over the different ways their data is tracked and collected by app developers of other companies. These point events do not happen in a void. This is a trend where Internet services are moving towards better security and privacy practices.
This trend is not limited to apps and the mobile world alone. It started way back with websites and their servers going secure. While going on a secure website makes your actions on that server secure, we at Dealarious firmly believe that online security should be end-to-end.
Government Surveillance Programs
Here are some of the noteworthy global surveillance programs available to solve online privacy issues and concerns.
Surveillance Program Name | Countries Involved | Program Description |
|---|---|---|
AUS, CAN, NZL, UK, USA | Intercepts communications between individuals. Flags individuals based on keywords and add them to a tracking list. | |
CHN | Automated + Manual Surveillance. The former covers sensitive topics like democracy, dissent, and Government criticism. The latter is carried out by officials and citizen volunteers who go through chat forums, emails, and blogs all day looking for content that poses any remote threat, direct or indirect, to the status quo of the Government. | |
DEU | Carries out global surveillance in close partnership with the CIA. This project collects photos, license plate numbers, search histories, and telephone calls of purported jihadists. | |
IND | Centralized Telephone Interception program operated by the Government of India. | |
RUS | ISPs are required to install a surveillance program on their servers to track credit card transactions, email, and browsing activity. ISPs must also connect their infrastructure to the FSB, the Russian federal security service. It has expanded to include social network traffic and chat forums. | |
SWE | The X-Keyscore program engages in both active and passive surveillance by monitoring and flagging certain race, sex, ethnicity, and geolocation specific to individuals. This lets X-Keyscore read specific user actions like email or telephone communications and expand it to multiple users based on this metadata, identifying potential future targets. | |
UK | GCHQ taps into undersea cables that carry Internet traffic in and out of the UK and analyzes it at GCHQ Bude station. This makes the UK the largest data collecting body. | |
US | Allows the NSA to monitor live communication over the video, audio, chats, and file transfers, and also access stored information in emails, photos, and social networks. It also collects data from Apple, Google, Microsoft, Facebook, and Skype. |
Here is a complete list of Government surveillance projects |
This list sounds like a conspiracy theory or a plot for a sci-fi movie. However, as a fact, the documents leaked by Edward Snowden confirm the existence of each of these programs. Governments have even confirmed the existence of some of these programs. In the media, too, various news publications have talked about them, and security journals have been covering them regularly. This is a reality we live in today. |
Where Does Online Privacy Apply?
Besides being magnificent, open, and massive, the Internet is also an unsecured network. If you do a quick search on Google for the term hackers steal data, the results will give you an estimate of what happens when you let your information float around unencrypted for the last month alone.

When it comes to online privacy, our primary privacy concern should be securing our sensitive account information from hackers and snooping governments. A common wrong notion among many people is that encryption is for those who have something to hide. Needless to say, encrypted connections are for everyone regardless of whether you have something to hide. You can encrypt your online data to protect it from hackers, the Government, and your ISP.
Without encryption, you are just another valuable collection of open data. It is an invitation for trouble.
Here are some findings according to a Pew Research Center survey conducted in 2019.
- 48% of Americans say they have little to no control regarding who can access the search terms they use
- 79% of Americans say that companies will not take responsibility in case misuse of data occurs.
33% of US internet users have some awareness of their country’s online privacy law
Online Privacy Issue: How Can we be safe?
In the above section, we have already mentioned that hackers and Government are the major threats to your online privacy. Now, there are many things you can take care of from your end. Taking small precautions can save you from a lot of trouble. You might already know these, but still, it is a good time to start now if you haven't already.
How to Protect your Online Privacy?

Choosing a good antivirus for your system is challenging. To help you out, we have curated some of the best antivirus programs that you can try and buy if it suits your needs.
Big Brother is Watching You!

There are no simple tricks to hide your data transfer from your ISP and, in turn, from the Government. At Dealarious, we believe that online anonymity and online privacy are about securing your entire online activity. There is only one family of tools that let us do this- VPN or Virtual Private Network. Find out how a VPN protects your privacy and anonymity.
How can I protect my online privacy through VPN?
VPN was originally designed for companies to overcome their geographic limitations. However, with the Internet, VPNs have also emerged to be a powerful privacy tool. A VPN not only hides your IP address but also your browser history from your internet service provider. If you are new to this term, you can learn more about what is a VPN.
Worldwide VPN Searches
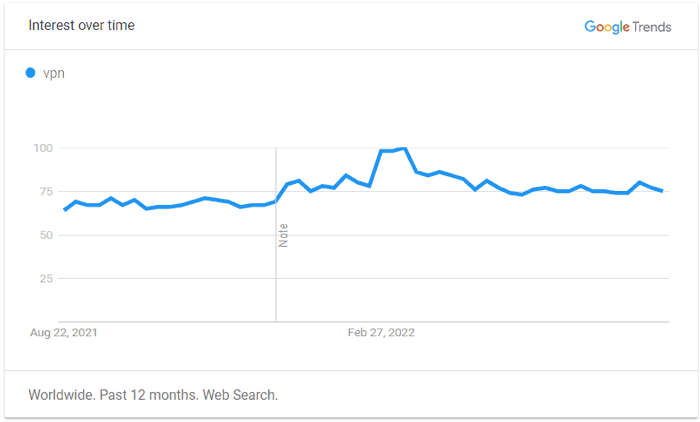
Updated in August 2022. Check latest update on Google Trends
A good VPN encrypts and helps you to stay anonymous online. Anyone spying on your connection will only see encrypted illegible characters. If you plan to buy one, you can select from any of the standalone VPN services like Surfshark, CyberGhost, or Private Internet Access VPN.
It is worth mentioning that a VPN alone is not enough to protect your online privacy. You should also consider some of the points mentioned above and other cyber security and privacy measures for complete privacy. Nonetheless, using a VPN is a necessary step toward protecting ourselves from online privacy issues.
Conclusion
Staying secure and private online is mostly about being in control of what data you send out from your device. The world is waking up to online privacy and related issues. It’s time we start being a part of this trend. Encryption standards are getting better every few years, and people are becoming more aware of online privacy issues as well.
Anonymity and online privacy are not just about keeping your identity secure online anymore. It could also cover bypassing geo-blocking for the frequent traveler. In cases like these, anonymity worries people more than privacy does. VPN services address all these issues seamlessly. They have evolved to be more robust, fast, and secure. Moreover, they all are super easy to use and start working at the push of a button.
Sourojit is Executive Editor at Dealarious. Rumor says He is Computer Science Engineer; He neither accepts it nor denies it. Tech Explorer, Philosopher and a Storyteller.